ICT, coming down in one continuous line with the "863 Plan" and the "973 Plan", is a long-term plan for the development and upgrading of China's IT industry. Its essence is to develop the domestic information industry, aiming to achieve the development goal of "independent, controllable, safe and reliable", and it is also the key to the digital transformation of the national economy and the promotion of the development of the industrial chain.
1、 Information innovation industry and information innovation software
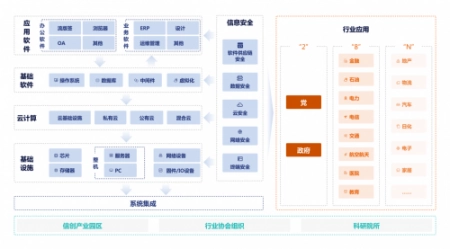
Information and innovation industry, namely information technology application and innovation industry, is a long-term plan for the development and upgrading of China's IT industry. The construction of information and innovation has been gradually promoted from the party and government pilot projects to key industries (2+8+N), gradually establishing independent IT infrastructure and standards, and optimizing and upgrading the strength and structure of the whole IT industry chain, mainly including IT infrastructure, basic software, application software and information security.
According to the relevant contents of the Central Committee of the Communist Party of China's proposal on formulating the 14th Five Year Plan for National Economic and Social Development and the Vision for the Year 2035, the 14th Five Year Plan of the People's Republic of China takes high-quality development as the theme, reform and innovation as the fundamental driving force, and accelerates the construction of a modern economic system. In the important direction of economic development, we should strengthen the construction of the domestic market, expand domestic demand, and actively develop strategic emerging industries, infrastructure and digital construction driven by innovation capability. The information and innovation industry is based on the information technology industry, and through scientific and technological innovation, building a domestic information technology industry ecosystem is an important starting point to achieve the development goals of the 14th Five Year Plan.
With the promotion of the information and innovation industry, China's basic software (including operating system, middleware, database, etc.) and application software market will have massive demand for information and innovation substitution and incremental procurement. According to statistics, taking the application software market as an example, the scale of China's ICT application software market will be about 594.44 billion yuan in 2022, and is expected to reach 1.5 trillion yuan in 2025, with a compound growth rate of about 35.1% from 2021 to 2025.
Figure Information Innovation Industry Chain
2、 "Two databases" are an important part of ICT software
"Two databases" are a general term for open source software library and security vulnerability library. They are an indispensable part of the information creation software. The open source software library has greatly improved the research and development efficiency of information creation software, while the security vulnerability library provides the information creation software with data support for known vulnerability detection.
(1) Open source software library: referred to as open source library, a network platform that publishes software source code according to the corresponding open source software license agreement. Any individual or organization can download and use all the functions of the open source software, or modify the source code according to their own needs, or even compile a derivative product and release it again, but they need to follow the open source license agreement, or they may cause intellectual property disputes. For example, in 2021, a science and technology company in Guangdong Province was sentenced to infringement and fined by the court for violating the source code authorization protection under the GPL3.0 agreement. In addition to the potential risk of open source license violations, the use of open source software may also face security problems. Synopsys pointed out in the 2022 Open Source Security and Risk Analysis Report that 97% of code repositories contain open source software, 81% of which contain vulnerabilities. The information and innovation industry is in the ascendant. Developing information and innovation software based on open source software can greatly improve development efficiency, but it also inevitably inherits the security vulnerabilities brought by open source software.
(2) Security vulnerability database: referred to as vulnerability database, it collects information security vulnerabilities of software and hardware systems such as basic software, application software, network equipment, etc. through active mining, social submission, collaboration and sharing, and establishes a standardized vulnerability research and disposal process, a smooth information sharing and reporting mechanism, and a sound technical cooperation system, It provides important technical support and data support for the security of important industries and key infrastructure. China's security vulnerability database mainly includes: CNVD (National Information Security Vulnerability Sharing Platform), CNNVD (China's National Information Security Vulnerability Database), etc. In addition, the international mainstream security vulnerability database also includes: CWE (Common Defect Enumeration Database), CVE (Common Vulnerability Disclosure Database), NVD (U.S. National Vulnerability Database), CVSS (Common Vulnerability Assessment System), etc. The traditional vulnerability detection tools of China's information innovation software rely on the vulnerability characteristics provided by the above vulnerability database to detect known vulnerabilities of information innovation software.
3、 Vulnerability challenges brought by "two databases" to ICT software
In July 2021, the Ministry of Industry and Information Technology, the State Internet Information Office and the Ministry of Public Security jointly issued the Regulations on the Management of Security Vulnerabilities of Network Products, which standardized the discovery, reporting, repair and release of product vulnerabilities; The responsibilities and obligations of various entities such as product developers, product service providers, vulnerability discoverers and vulnerability publishers are clarified. The rapid growth of the ICT software market has spawned a large number of ICT software codes, products, developers and service providers. However, the proliferation of Xinchuang software will inevitably lead to the proliferation of its security vulnerabilities. Controlling the number, destructiveness and scope of impact of security vulnerabilities and ensuring the credibility and security of information technology software are not only the explicit requirements of laws and regulations, but also the basis of the entire information technology security system, which has become an urgent problem to be solved.
As an important part of information creation software, open source software library and security vulnerability library bring security vulnerability challenges to information creation software while improving the research and development efficiency of information creation software and providing data support for known vulnerability detection:
(1) Xinchuang software development relies heavily on open source software, but lacks sufficient understanding of the security vulnerabilities of open source software. Unclear information about the dependency, scope of influence, degree of damage and other information of open source software security vulnerabilities will bring great security risks to the information creation software.
(2) Influenced by the open source community and restricted by international relations, the underlying architecture and the third-party components relied on by the information innovation software may face the risk of supply interruption. If the open source license agreement is not followed, intellectual property disputes may also arise.
(3) In the face of the surge of Xinchuang software code and products, there is a lack of matching security vulnerability detection capabilities and means: relying on manual detection, detection efficiency cannot cover the growth rate of code. The detection depends on the vulnerability characteristics provided by the vulnerability library. However, due to the differences in the technical architecture and operating environment between the information creation software and the general software, CVE, NVD, CNVD, CNNVD and other general vulnerability libraries are not fully applicable to the information creation software.
4、 Strengthen the capability of software component analysis in the face of open source software
The information and innovation industry is in the ascendant. Research and development based on the open source software provided by the open source software library can significantly improve the research and development efficiency of information and innovation software, but this way will not only inherit the security vulnerabilities from the open source software, but also follow the relevant open source license agreements such as GPL/LGPL/BSD, or it may cause supply interruption risk and intellectual property disputes.
To solve the above problems, software composition analysis (SCA) is the most effective technical means. Software composition analysis is a technology to identify, analyze and track the components of binary software, which is specially used to analyze various source codes, modules, frameworks and libraries used by developers, to identify and inventory the components of open source software and their composition and dependencies, and to identify known security vulnerabilities or potential licensing problems, The troubleshooting of these risks before the software system is put into production is also applicable to the diagnosis and analysis of software system operation. It can be described as follows:
(1) Software bill of materials analysis capability: scan and generate the list of open source software that appears with the information creation software, including all dependencies resolved in the construction phase. This output is the software bill of materials, usually including: software name, software version, source or distribution, file path and other information.
(2) Risk management capability of open source license agreement: analyze the license agreement of open source software, clarify its commercialization restrictions, help standardize the use of open source software, and avoid the risk of supply interruption and intellectual property disputes caused by Xinchuang software due to political reasons or violation of the open source agreement.
(3) The known vulnerability detection capability of open source software: based on the security vulnerability library, compare the known vulnerability characteristics of the open source software version in the software bill of materials, identify the known vulnerability of the open source software, and analyze the security risks of the vulnerability to the information creation software.
(4) Open source software unknown vulnerability mining capability: based on fuzzy testing technology (see Chapter 5 for details), open source software versions in the software bill of materials are mined for unknown vulnerabilities to supplement the unknown vulnerability detection capability that the security vulnerability database does not have.
5、 Based on fuzzy testing, complement the weakness of vulnerability detection capability
Based on the known vulnerability characteristics provided by the security vulnerability database, known vulnerability detection can partially solve the security vulnerability problem of information creation software. However, in order to effectively guarantee the credibility and security of the information creation software, the following aspects still need to be improved:
(1) Lack of special vulnerability database for information and innovation software: information and innovation software is an emerging product in recent years, and it is different from the technical architecture and operating environment of general software. CVE, NVD, CNVD, CNNVD and other general vulnerability databases lack vulnerability accumulation for information and innovation software, and the existing vulnerabilities are not fully applicable to information and innovation software. We need to accumulate vulnerability databases specifically for information and innovation software, Provide more accurate technical support and data support for the vulnerability of the information creation software.
(2) Reduce the false alarm rate of known vulnerabilities of the information creation software: based on the known vulnerability characteristics provided by the vulnerability database, known vulnerabilities can be quickly identified, but on the other hand, a large number of false alarm information is inevitably caused. We need to optimize the vulnerability detection mechanism and supplement the vulnerability location and recurrence capabilities, so as to reduce the false alarm rate of the vulnerability of the information creation software and improve the vulnerability handling efficiency.
(3) Improve the ability of Xinchuang software to mine unknown vulnerabilities: through comparison of known vulnerability characteristics, known vulnerabilities can be found, but there is nothing to do about unknown vulnerabilities. And the accumulation of known vulnerability characteristics is also the source and the discovery and analysis of unknown vulnerabilities. Therefore, the mining of unknown vulnerabilities is the underlying capability of vulnerability detection of Sinotron software, and it is also our most missing capability at present, which needs to be improved urgently.
In the face of the above improvement requirements, fuzzy testing is the most effective technical means. Fuzzy testing is a kind of software automated testing technology. It constructs random and unexpected abnormal data as the input of the program, monitors the exceptions that may occur during the execution of the program, and then uses these exceptions as the starting point of analysis to determine the availability of vulnerabilities.
In 1988, Professor Barton Miller introduced the concept of fuzzy testing for the first time in a test project aimed at the quality problems of UNIX operating systems. Testing by inputting a large number of completely random data can cause most software to crash. Although the effect is significant, there are still problems such as low test efficiency and unstable vulnerability output.
In 2013, AFL (American Fuzzy Lop) was released. This is an intelligent fuzzy testing technology based on coverage guidance. It explores the internal execution path of the program by inserting piles at compile time, so as to improve the code coverage and improve the low efficiency and unstable vulnerability of traditional fuzzy testing technology. Huawei, Microsoft, Google and other enterprises began to apply fuzzy testing technology in a wide range, and achieved extremely significant results. However, because the technical threshold is too high, the fuzzy test technology can only be applied in the large head factories at present.
In 2021, Beijing Yunqi Wuyin Technology Co., Ltd. was established. The founding team was born in Tsinghua University. Over the years, while optimizing the fuzzy test algorithm, it also significantly reduced the threshold for the use of this technology. Yunqiwuyin is committed to producting fuzzy testing technology, so that more enterprises can enjoy the convenience of fuzzy testing technology. Its products have the following advantages:
(1) Massive test cases: AI genetic algorithm is used to assist intelligent mutation of test cases. Based on the feedback learning mechanism, massive (billion level) test cases are automatically generated to detect the security of target software and improve the software detection coverage.
(2) False alarm rate is zero: based on the memory level fine-grained detection capability and dynamic execution verification capability, the false alarm rate of product detection defects is infinitely close to zero, and the software defects found can be located, reproduced and verified.
(3) Discovery of unknown defects: through the security detection of the running state of the software, the coverage guided technology is used to guide the variation of test cases, trigger the abnormal branches that are easily ignored by traditional detection methods, so as to discover unknown defects.
(4) Reduce labor cost: carry out automatic dynamic detection for software, without manual participation in the intermediate process, greatly improve detection efficiency and reduce labor cost.
In the future, based on fuzzy testing, software composition analysis and other technologies, Yunqiwuyin will focus on the software supply chain security field and be committed to solving known and unknown vulnerabilities and other threats of software (open source, closed source). At the same time, we will continue to improve various solutions, provide security assistance for the development of the information and innovation industry, and promote industrial upgrading and development. (Cui Zhuo, CTO of Boundless Clouds)