Open Phoenix News to view more HD pictures
Every day, we connect with resources through more and more rich Web applications. Research shows that most users are unwilling to "give up the Internet" in exchange for "preventing personal information leakage". Therefore, the Web server has become the main target of the attack because of its powerful computing power, processing performance and holding these valuable information. According to statistics, 64% of companies have suffered attacks from the Web. 62% of companies have been attacked by phishing or social engineering. In addition, 59% of companies have been attacked by malicious code and botnets.
For enterprises, protecting the security of high value enterprise websites and stored data is the top priority. However, after the establishment of the website, we will find that no matter how complete the configuration is, the website will also encounter various attacks and scans, and the server seems to be the hot cake of streaking. If you have never met the precedent of malicious attackers or information theft before, you will never understand how serious the consequences of such things are and how close the risk is to us. What should I do?
Inertial thinking will tell us that we should install a firewall, but which option is better? Hardware firewall? Software firewall? Web application firewall? If you are not a professional, you will be bewildered by the variety of products on the market. To figure out what kind of firewall to choose, starting from the needs is the best way. What problems do we hope the firewall can help us solve?
First, we need to sort out the requirements:
1. It should be able to defend against malicious attacks from the network: to prevent malicious attacks from competitors or extortion by hackers, resulting in request timeout, instant break, instability and other problems.
2. It is necessary to prevent data leakage: prevent hackers from invading website databases and obtaining core business data through SQL injection, web trojans and other attacks.
3. It is necessary to prevent corporate websites from being tampered with: prevent hackers from affecting website image by scanning system vulnerabilities, modifying page content or publishing bad information after embedding trojans.
4. To meet the security compliance requirements required by the government: meet the requirements of relevant laws and regulations, and meet the requirements of information system security level protection (equal protection evaluation).
Next, let's learn about firewalls.
1、 Traditional firewall (FireWall)
When we access the Internet, the firewall is a kind of software and hardware equipment used for security management and screening. It separates the internal network from the public network (such as the Internet) and helps the computer network build a relatively isolated protective barrier between its internal and external networks to protect user data and information security.
The hardware firewall is easy to understand. It is usually a rectangular flat box. It solidifies the firewall program into the chip, and the hardware performs these functions, thus reducing the burden on the CPU and making the service more stable. The hardware firewall may have other functions besides the software firewall, such as CF (content filtering), IDS (intrusion detection), IPS (intrusion prevention), VPN, etc., which results in the high price of the hardware firewall.
The software firewall is to deploy software on the system host to complete the firewall function. Its security is worse than the hardware firewall. At the same time, it takes up system resources and affects the system performance to a certain extent. It is generally used in stand-alone systems or very few personal computers, and rarely used in computer networks.
The key technologies of firewall mainly include filtering technology, encryption technology, anti-virus technology and proxy server. The main functions include network security barrier, strengthening network security strategy, monitoring audit, preventing internal information leakage, logging and event notification.
2、 Web Application Firewall
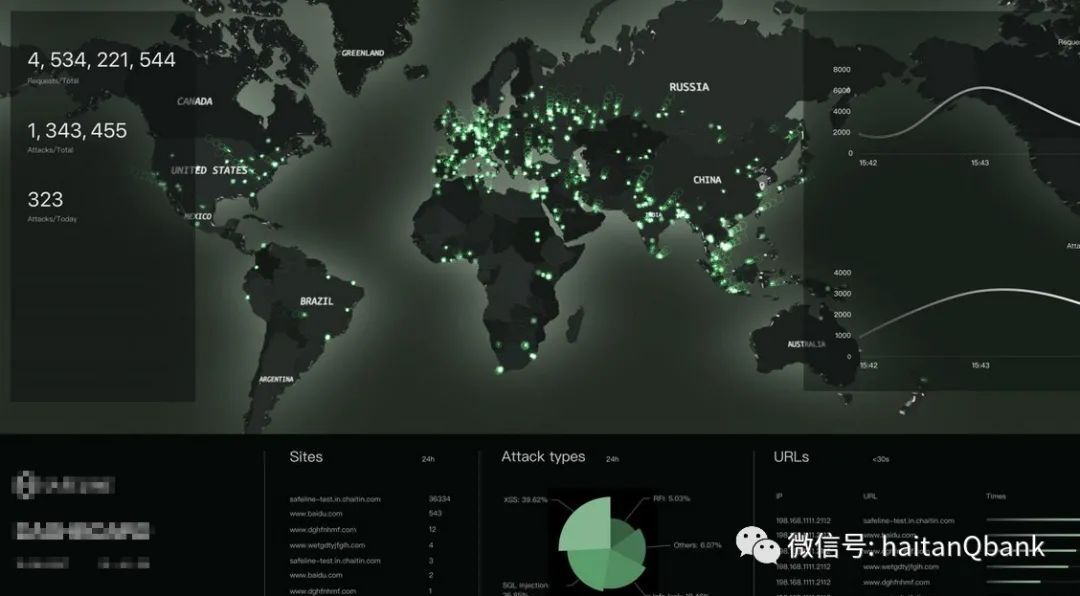
The lower network layer (Web application firewall is placed in the seventh layer) is covered by many devices, each of which has its own unique functions, such as routers, switches, firewalls, intrusion detection systems, intrusion prevention systems, and so on. However, in the HTTP world, all these functions are integrated into one device: Web application firewall. Web application firewall is mainly capable of protecting against Web specific intrusion modes, such as common DDOS protection, SQL injection, cross site script attacks, parameter tampering, application platform vulnerability attacks, denial of service attacks, etc. Since all the intrusions belong to the application layer rather than the network layer, they belong to the Web IPS (Web Intrusion Prevention System) rather than the traditional firewall technically.
The Web application firewall is deployed in front of the Web application, scanning and filtering user requests before they reach the Web server. The Web application firewall analyzes and verifies the network packets requested by each user, records the hacker attack sample library and vulnerabilities, and uses thousands of defense devices and backbone networks, as well as security avatars, attack traceability and other cutting-edge technologies, Ensure that each user's request is effective and secure, build a website application level intrusion prevention system, block or isolate invalid or aggressive requests, solve abnormal problems such as webpage tampering, data leakage and unstable access, and ensure website data security and application availability. The emergence of Web firewall has solved the problem of application layer attacks that traditional firewalls cannot solve.
What kind of firewall should I choose?
From the above analysis and description, we can see that traditional firewalls only block some underlying (network layer, transport layer) information, while Web application firewalls go deep into the application layer, filter all application information, solve the application layer protection problems that traditional firewalls cannot solve, and provide the following functions:
Attack protection: Intelligently identify the service status of the Web system, optimize the defense rule base online in real time, distribute virtual patches, and provide continuous security defense support. Thousands of defense devices, hundreds of gigabytes of massive bandwidth and internal high-speed transmission network can effectively resist various DDoS attacks and CC attacks in real time.
Security avatar: through the cutting-edge security avatar technology and virtual patch service, the web security problem is invisible by means of active discovery and collaborative defense. Even in extreme cases, when the Web system is invaded or even completely destroyed, the security content can be reconstructed to ensure the normal service of the system.
Traceability of attacks: There are 300000 hacker archives and vulnerability service centers around the world to conduct real-time interception and linkage dynamic analysis of attacks. Trace the attackers and events through the big data analysis of the 10 billion log, and use the "reverse APT" technology to improve the hacker archive, providing a detailed basis for attack forensics.
Login security: The login security of the Web system is realized by associating the failed user name, password, login frequency, post login geographical changes and other factors.
The iterative web application firewall will have more powerful capabilities, such as: web source code encryption, anti scanning, anti automation attacks, anti brute force cracking, anti-collision library, anti sniffing, etc.
Complexity of Web security requirements
In a broad sense, Web application firewall is an application level website security comprehensive solution, but it is difficult to define, because the name contains too many things. If we want to study its precise definition, we may get more questions. Because some Web application firewalls are hardware devices, and some are application software; Some are based on the network, while others are embedded in the WEB server. People with different knowledge backgrounds tend to pay attention to its characteristics in different aspects. For example, people with network intrusion detection background tend to regard it as an IDS device running on the HTTP layer; People with firewall background tend to regard it as a function module of firewall. Another understanding comes from the term "deep detection firewall". They believe that the deep detection firewall is a device with the same function as the Web application firewall. However, although there are some similarities between the two devices, there are still great differences. The deep detection firewall usually works in the third layer and higher layer of the network, while the Web application firewall handles HTTP services in the seventh layer and supports it well.
From a technical point of view, it is better to directly change Web code to solve security problems, which is beyond doubt, but it is not so easy (implementation). Because it is controversial whether the security performance of the system can be enhanced by changing the WEB application code. And the reality is more complex:
1. It is impossible to ensure 100% safety. People's limited ability will inevitably make mistakes.
2. In most cases, few people seek 100% safety. In today's real life, those who lead the development of applications pay more attention to function than security. This concept is changing, but slowly.
3. A complex system usually contains third-party products (components, function libraries) whose security performance is unknown. If the source code of this product is confidential, you must rely on the manufacturer of the product to provide patches. Even if the source code is open in some cases, you can't have the energy to fix it.
4. We have to use business systems with security risks, although these old systems can't be improved at all.
Therefore, if enterprises want to achieve the best results, we need to do both: on the one hand, we must improve the security awareness of managers and developers; On the other hand, improve the security of the application system as much as possible.


